How to manually delay Windows updates
Windows 10 update settings are varied and at times confusing. Here is an exact listing of the settings that I use that allows me to control exact when updates will automatically updated on my systems. You can use these Windows Update for Business settings either on a standalone workstation, in group policy, via registry entries and finally in conjunction with Windows Software Update Services (WSUS). Note these settings are current as of 1803 on Windows 10.
To set Windows update to install a set number of days after they are released you need to set the Windows update for Business settings to defer quality updates for a set number of days. Given the side effects of updates, I recommend waiting at least 7 days if not more before installing quality (security) updates. If you choose a deferral of 11 days this pushes the update window past the weekend and on to the second week when most of any side effects are identified.
The second deferral I recommend is the installation of Feature Update to a time and date that you feel is right for your environment. I also recommend scripting the install of the Feature updates as a better way to control the install of Windows 10 feature releases. Microsoft releases feature releases and (at this time) calls the release semi-annual (targeted). Then when the feature release is deemed ready for business, the release is declared Semi-annual. By default if you take no action to control updates, the feature releases are set to semi-annual (targeted) and you will receive the feature releases when your computer is deemed by Microsoft to be ready for the update. Feature updates do not include security updates and thus it’s quite safe to push off feature updates to ensure that your vendors support the release. These deferrals can be set on Windows 10 Pro, Enterprise and Educational versions.
Tip: If you manage group policy in a domain setting be sure you download the Windows 10/Server 2016 templates to your domain by copying the ADMX files from any recent Windows 10 workstation to the server group policy settings to the SYSVOL central store:
DeliveryOptimization.admx from C:Program Files (x86)Microsoft Group PolicyWindows 10PolicyDefinitions
DeliveryOptimization.adml from C:Program Files (x86)Microsoft Group PolicyWindows 10PolicyDefinitionsen-US
The following settings can be set under Computer Configuration, Administrative Templates, Windows Components, Windows Update
Under Windows Update for Business set the following settings:
Select when Preview Builds and Feature Updates are received: Set this to Semi Annual Channel and then set the deferral of feature updates to 360 days. This pushes off the installation of any Feature release to nearly a year after a Feature release is declared Semi-Annual. I recommend setting it this far in the future and then you actually install the feature release when you deem it ready for your environment.
Under Computer Configuration, Administrative Templates, Windows Components, Windows Update, Choose Select when Quality updates are received and set this to at least 7 days, and even consider setting it for 11 days. This pushes off when Quality updates are installed and if you choose 11 days this pushes off the install to two weekends after the security updates are released.
The following settings should be set as well under Computer Configuration, Administrative Templates, Windows Components, Windows Update,
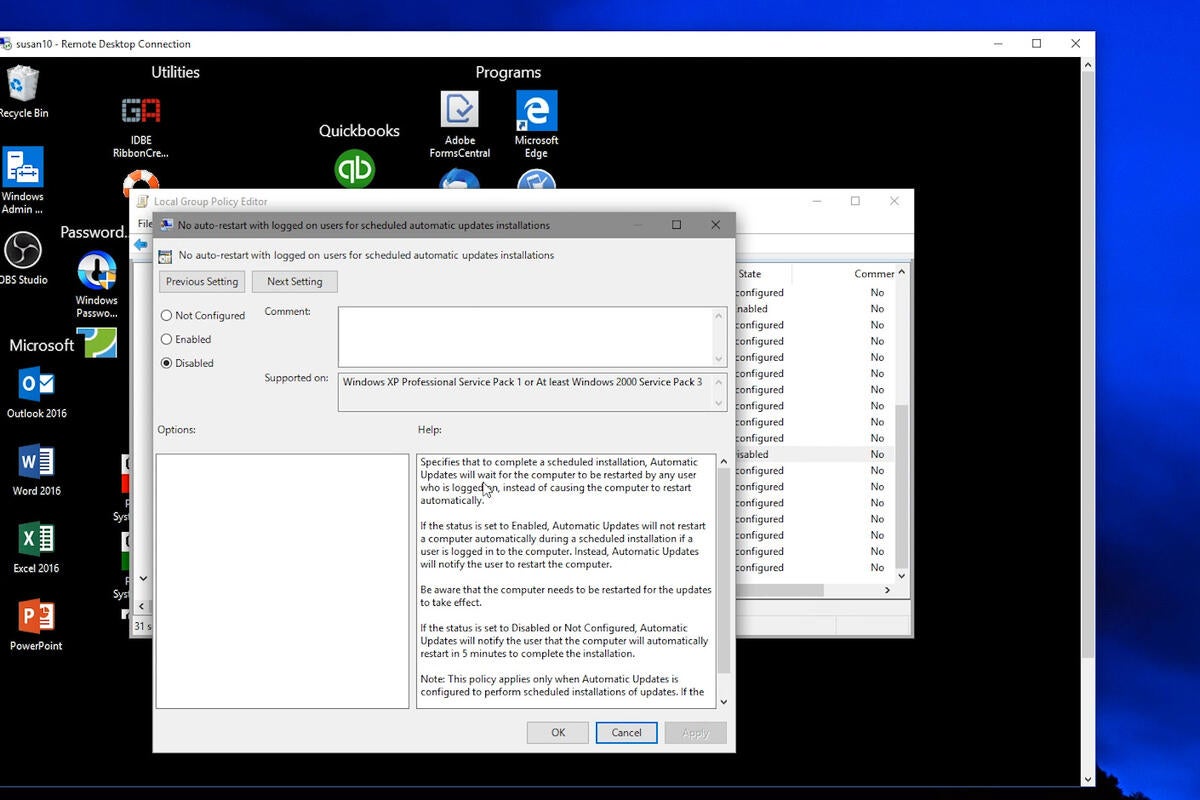
Do not use or set the policy for No auto-restart with logged-on users for scheduled automatic update installations. This policy in my experience does not properly detect a logged on user and often will trigger a reboot of the system when a user walks away from the computer and does not respond to a notice on the screen. Thus I do not recommend this setting to be used in conjunction with Windows 10 at all. When I have used it in conjunction with WSUS settings I end up with machines that reboot at awkward times and do not reboot when I want them to reboot.
If you use Windows Software Update Services, ensure that you set and use Do not allow update deferral policies to cause scans against Windows Update. Without this setting in place, if you set any feature deferral policy, it will bypass your WSUS settings and go directly to Microsoft updates for any updates. The end result will be that your WSUS settings for not approving Windows 10 updates and feature updates will be ignored and updates will be applied.
The next setting to use is to set the active hours. Enable Turn off auto-restart for updates during active hours. The maximum number of hours to set is a period of 18 hours. This will ensure that restarts will be outside of the active hour of the machine. Note that the notes of the policy states that if no-auto restart with logged on users for scheduled automatic updates installation is enabled then the active hours setting will be ignored.
Finally you can set the settings for “Engaged restart” whereby users will get notifications and prompts regarding the pending updates. As noted if any of legacy Windows update settings are selected such as No auto-restart with logged on users for scheduled automatic updates installations, always automatically restart at the scheduled time or Specify deadline before auto-restart for update installation – any of these updates will nullify this engaged restart settings so ensure you do not set any of those settings with Windows 10.
These settings are key to having successful control of Windows update on Windows 10.

